Azure tagging can be incredibly useful. It can be used to classify different Azure resources as well as providing a method for cost analysis outside the normal scopes of management groups, subscriptions and resource groups. However, for tagging to be effective, all resources need to be tagged. Very often I’ve seen tags have been missed or incorrectly applied leading to inaccurate cost analysis (or classification).
For customers I’ve worked with recently I’ve found using Azure Policy to append tags to all resource groups and then setting all resources to inherit the tags and their values a great method to ensure all resources are tagged correctly.
NOTE: To perform the steps below your user will need to have Azure Policy permissions over the scope you’d like to tag. In my example I’m an Owner (which is the highest level of permissions and required for creating the managed identity for remediation).
Create the new Initiative
In the Azure Portal, go to ‘Policy’
In Azure Policy, go to Authoring, Definitions and + Initiative Definition. An initiative is a collection of policies.
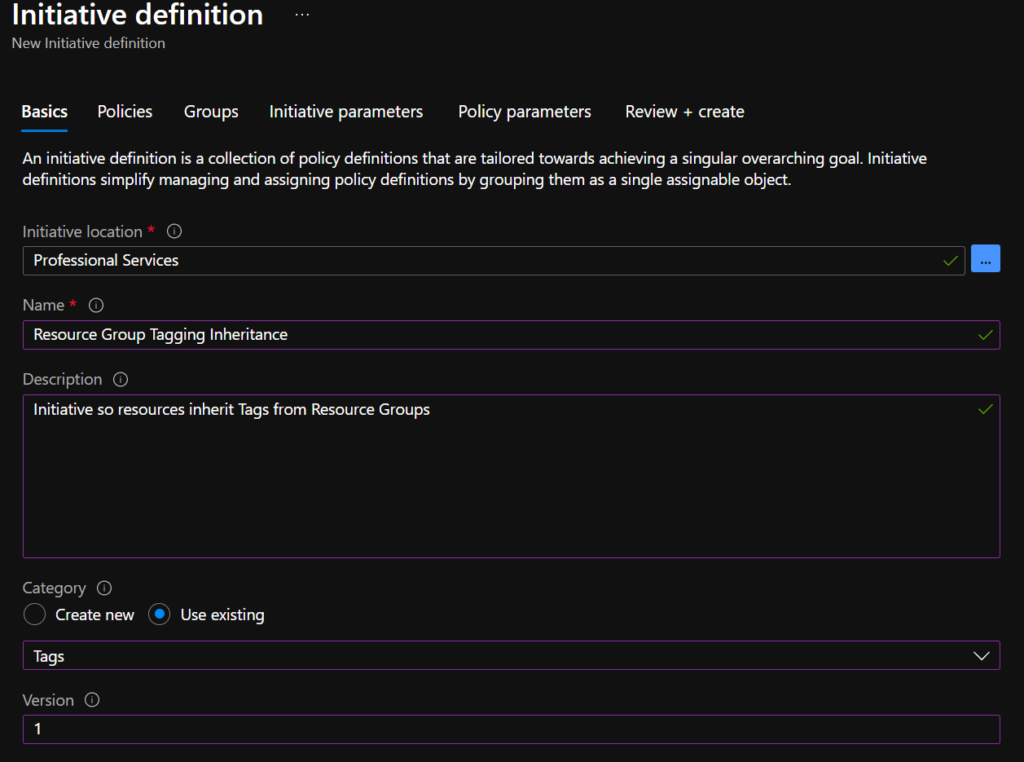
Set the Initiative location to the location that you would like to apply your new tagging. For example, a subscription or management group.
NOTE: Management groups are collections of subscriptions (think similar to OUs in Active Directory) but need to be set up. More info here:
https://docs.microsoft.com/en-us/azure/governance/management-groups/overview
Give a suitable name and if required, a description, Category and Version.
In the policies tab add for each tag ‘Append a tag and its value to resource groups’ and ‘Inherit a tag from the resource group’. In this example I have 3 tags, ‘Application’, ‘Environment’ and ‘Owner’ so have three instances of each policy:
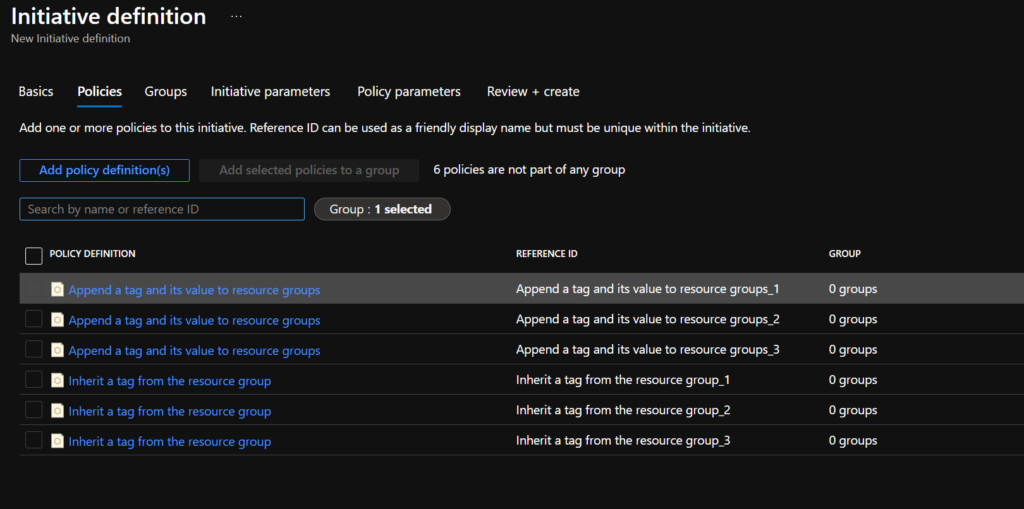
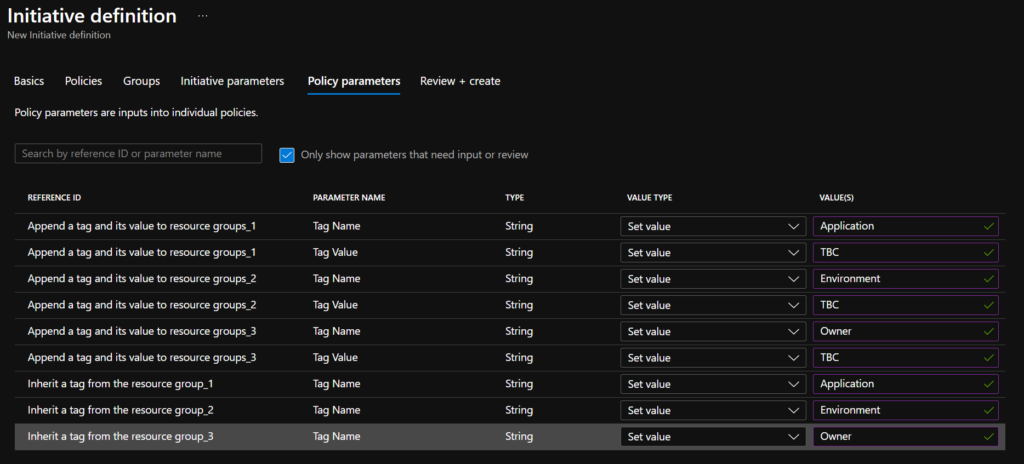
Leave ‘Groups’ and ‘Initiative parameters’ tabs as default and go to ‘Policy parameters’. Populate with default Tag Names and Values as below:
Go to ‘Review + Create’ and click Create to create the new Initiative.
This initiative is designed therefore to Add tags ‘Application: TBC’ ‘Environment: TBC’ and ‘Owner: TBC’ to each resource group. It would then be recommended to change the values of these tags on the resource groups to more relevant values (rather than TBC). Any new resources deployed to these resource groups will then inherit the tags!
Assign the Tagging Initiative
Next step is to Assign this new initiative to the Management Group/Subscription/Resource Group that we would like this tagging to take place. In my example I’m going to assign it to the management group ‘Professional services’ (which is the same location as the Initiative definition).
To assign navigate to Azure Policy and under Authoring – Assignments. Click Assign initiative
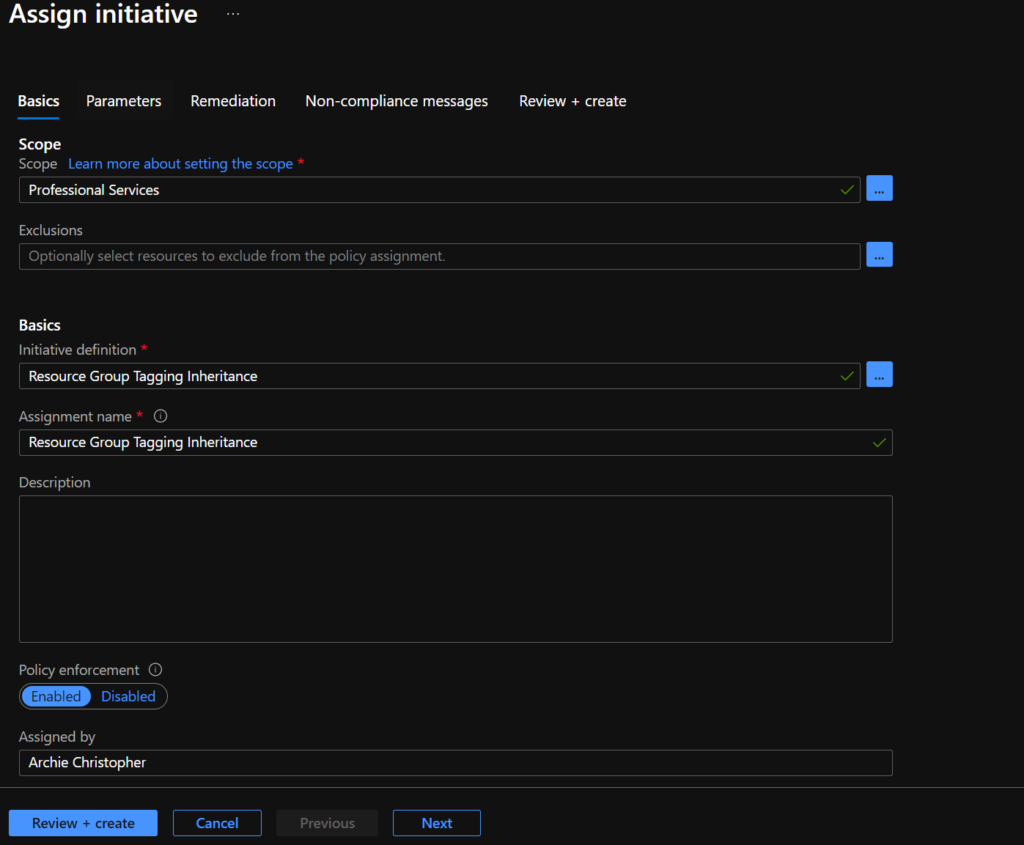
On the ‘Remediation’ Tab the assignment will prompt you to create a managed identity to perform the tagging remediation. (see next section). Change the location to the region that your Azure resources will reside.
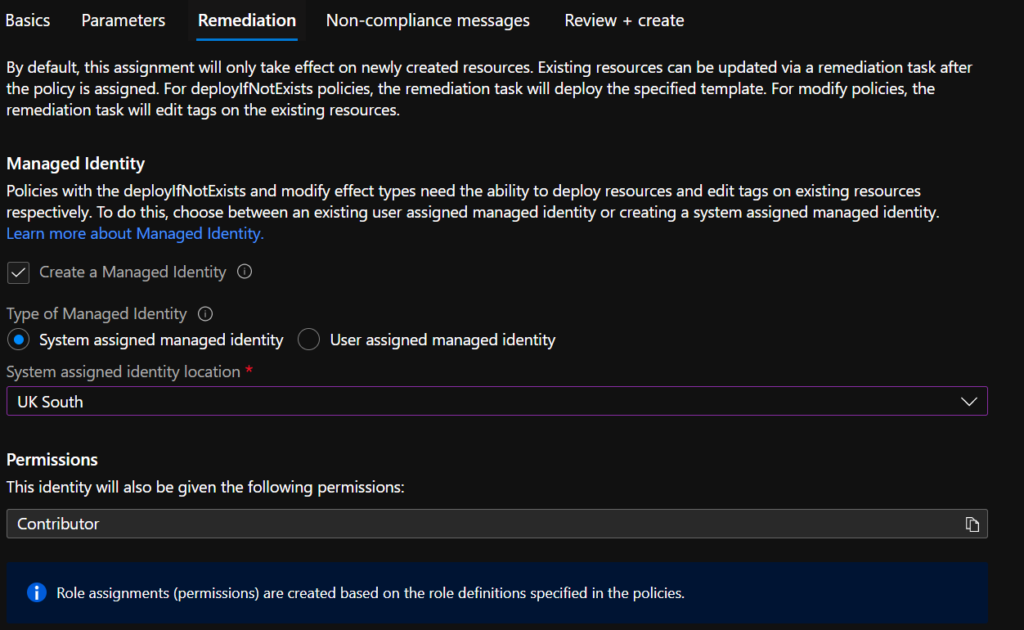
Select Review + Create and create your assignment.
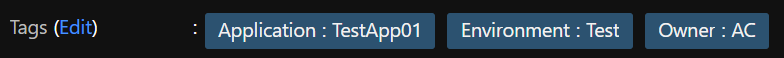
After this is done, you can create test resource groups in your assignment scope and you should see the tags (with default values of TBC) automatically applying. If you then change the tags to relevant values, any resources then deployed to these resource groups will inherit these Tags. E.g.
Modify Managed Identity Permissions (Recommended)
On creating the assignment of the initiative Azure will create an Enterprise Application in Azure AD to act as a managed identity to perform tagging remediation. It will by default grant that identity ‘Contributor’ permissions over the scope which, in this tagging scenario, is more permission than required. You can change this to be ‘Tag Contributor’ by following the steps below:
Navigate to the subscription/management group where the Azure Policy Initiative has been assigned. Select ‘Access Control (IAM)’ from the side bar.
Select the ‘Role Assignments’ Tab and identify the App which has been automatically granted contributor rights:
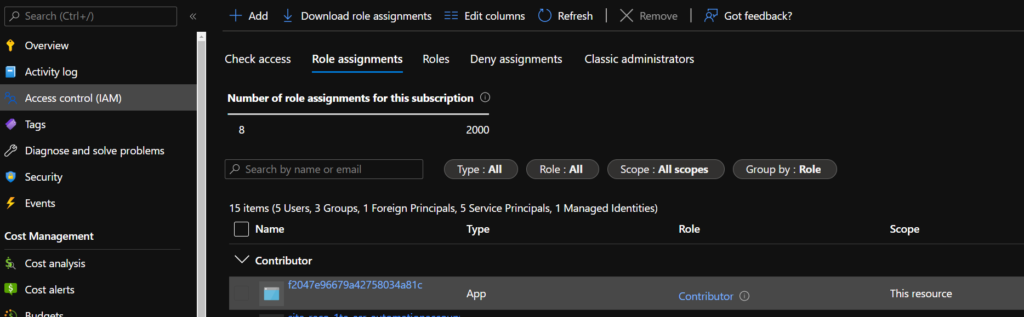
Take a copy of the Name (it will be a random string).
Click + Add to add a role assignment.
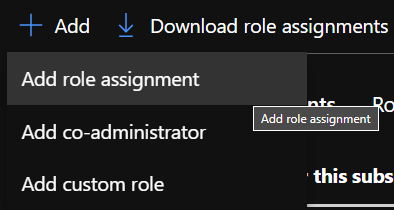
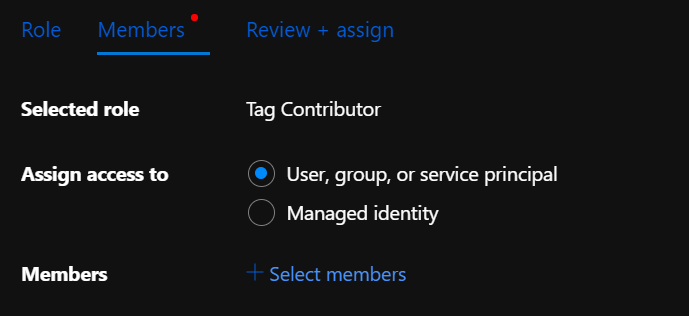
Select Role ‘Tag Contributor’ and in the Members tab select ‘User, group or service principal’ and click ‘Select Members’ to search for the name of the App.
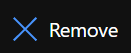
The app will now appear twice in the Role Assignments – once as contributor and once as tag contributor. Remove the ‘Contributor’ entry by checking the box next to that Role Assignment and selecting ‘Remove’ from the top bar.
Running Remediation Tasks to update modified Tag Values
Now the Initiative has been assigned, all new resource groups will automatically get Tags of ‘Application’, ‘Environment’ and ‘Owner’ with default values ‘TBC’. Any new resources deployed will automatically inherit these tags.
HOWEVER if Resource Group Tag Values are modified after resources have been deployed, a remediation task is required to update all resource tag values (using the Enterprise application created in the assignment).
To configure a remediation task to do this, go to Azure Policy and select ‘Compliance’ from the side-bar.
Select the Tagging Inheritance Initiative created earlier from the list. If Tag values on resources don’t match those on resource groups, the initiative should be listed as ‘Non-compliant’. If this isn’t the case, then the resources may need to be scanned by the Policy engine which happens every 24 hours by default or can be manually triggered (see next section):
Select ‘Create Remediation Task’
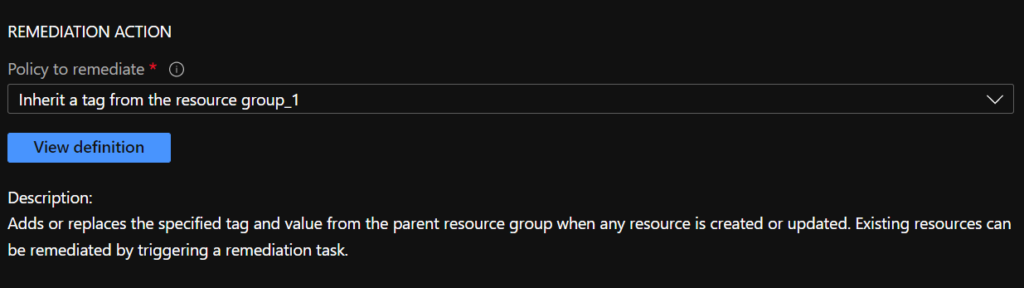
Select which Policy to remediate (each policy number corresponds to a tag, so you may need to check the Initiative definition to see which number corresponds to which tag). In this example, I’m going to remediate the ‘Application’ tag which corresponds to the policy ‘Inherit a tag from the resource group_1’
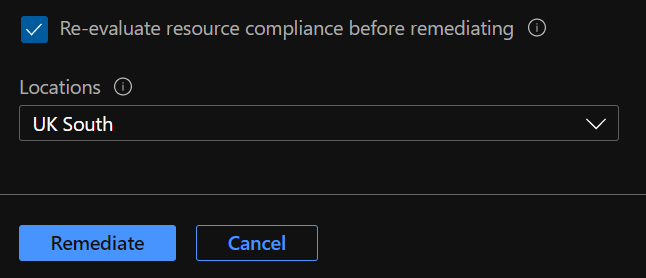
Ensure the scope is correct and check the box ‘Re-evaluate resource compliance before remediating’. Select the relevant Locations (if necessary) Click Remediate.
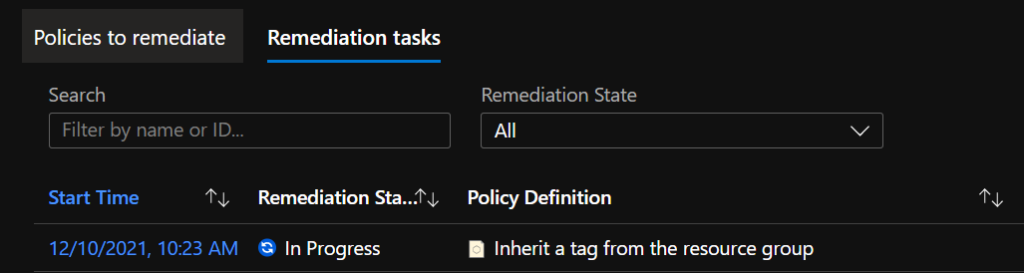
In Azure Policy in the Remediation section under ‘Remediation tasks’ you will be able to monitor the remediation task:
Once complete, tag values will be updated and the initiative compliance should be back to ‘Compliant’.
Manually Triggering Policy Scan
There are a number of ways to manually trigger a policy scan on your resources.
Using Azure CLI (either in cloud shell or on your local computer), you can run:
az policy state trigger-scan
As scans can take some time to complete, you can also narrow down the scope of the scan to a resource group:
az policy state trigger-scan –resource-group “ResourceGroupName”
Powershell can be used as an alternative. Once logging into Azure Powershell in the correct subscription, run the following command:
Start-AzPolicyComplianceScan -ResourceGroupName ‘ResourceGroupName’
More information on how to run policy scans is on Microsoft docs here:
https://docs.microsoft.com/en-us/azure/governance/policy/how-to/get-compliance-data
Adding Policy to Audit for Tags with value ‘TBC’ (Optional)
A final addition to this tagging solution is to add a custom policy which audits for tags of values of ‘TBC’, meaning that you can identify which resources haven’t had their tags updated from the default TBC.
To do this, go to Azure Policy, Definitions and create a new Policy Definition:
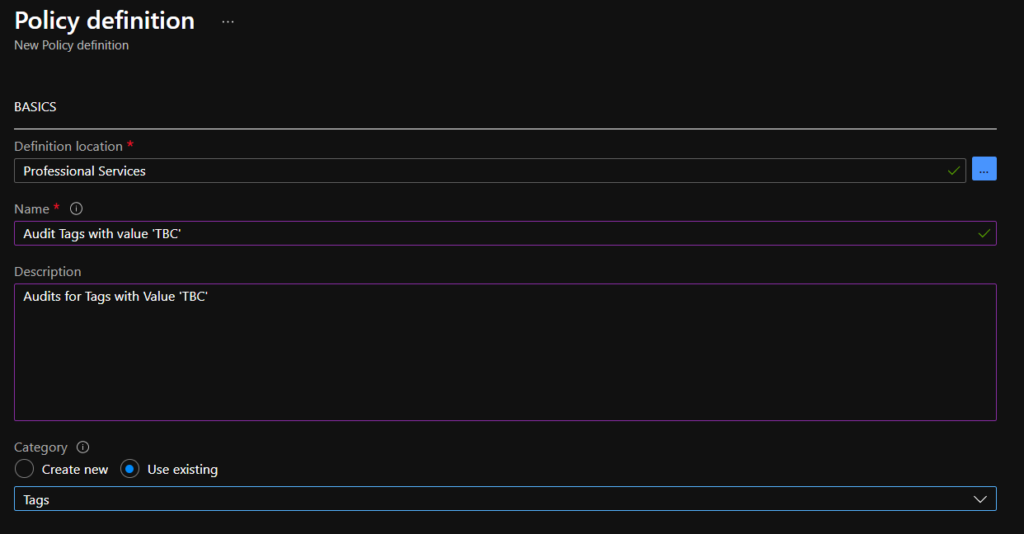
Set the location as the same as the Initiative created earlier, give relevant name, description and category:
Use the following JSON, modifying and tag names as appropriate.
{
“mode”: “Indexed”,
“policyRule”: {
“if”: {
“anyOf”: [
{
“field”: “tags[‘Application’]”,
“equals”: “TBC”
},
{
“field”: “tags[‘Environment’]”,
“equals”: “TBC”
},
{
“field”: “tags[‘Owner’]”,
“equals”: “TBC”
}
]
},
“then”: {
“effect”: “audit”
}
},
“parameters”: {}
}
Click Save.
Add this policy to the same initiative assigned at the subscription/management group earlier, by going to Azure Policy – Definitions – Tagging Inheritance Initiative and Edit Initiative.
Add this new policy to the policies tab and then Save.
Now after the next policy scan/evaluation (either wait 24 hours or run the commands as discussed in the previous section) you will see listed in Azure Policy – Compliance the resources listed with Tags set to TBC.
You can then remediate by modifying tag values at resource group levels and then setting up remediation tasks to tag all resources correctly.

Great content! Keep up the good work!
Excellent stuff, thanks.